We infiltrated a survey scamming ring. Here's what we found.
- Omar

- Aug 29
- 4 min read
There's a multi-million dollar economy built on cheating market research surveys, and it's operating openly online. I went undercover in the survey scamming communities that operate openly on Reddit, Telegram and Twitter.

If you're involved in market research, you've seen the impact of fraud firsthand. But to truly combat it, you need to see it from the inside.
The Wild West of Survey Fraud
Communities like r/cheatingsurveys on Reddit, t.me/Surveyofficial on Telegram and Twitter have created entire ecosystems dedicated to gaming survey systems for profit.
These communities operate in plain sight, with thousands of members openly discussing fraud tactics in a manner that can only be described as supportive and collaborative. A lot of the big players were happy to describe their process in detail to me, little did they know SuperMarketer specialises in blocking just this sort of behaviour.
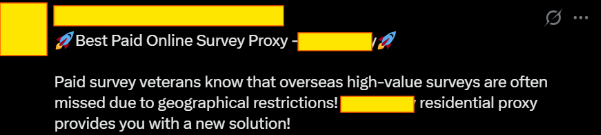
The Toolkit of Survey Scammers
The community regularly recommends specific tools designed to evade detection:
Multi-Identity Browsers: Platforms like GoLogin and MoreLogin are heavily promoted, allowing users to create multiple browser fingerprints and manage dozens of fake identities simultaneously. Each "identity" can complete the same survey multiple times, multiplying payouts.
Demographic Optimization: Thought leaders in the space share detailed intelligence about which demographics and job titles trigger higher-paying surveys. They've essentially reverse-engineered market research targeting to maximize their fraudulent earnings.
Coordinated Information Sharing: Members actively share "winning" demographic profiles, survey company vulnerabilities, and real-time tips about which surveys are currently paying out the most and how to navigate their anti-bot techniques.
Why Traditional Security Measures Don't Work
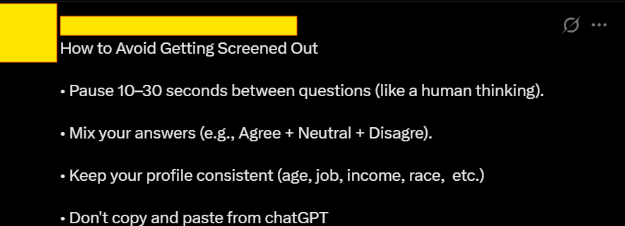
What is immediately apparent is how easily these scammers bypass supposedly secure verification systems that many companies rely on. Most posts on Telegram, specifically reference what checks each survey has put in place with instructions on how to bypass them.
CAPTCHA is Dead: Services like 2Captcha offer to solve CAPTCHAs for as little as $1 per 1000 challenges, while AI-powered solutions like NopeCHA can bypass them automatically. The survey fraud communities openly recommend these services, treating CAPTCHAs as a minor inconvenience rather than a real barrier.
KYC can be gamed: Traditional identity checks, especially those relying solely on document scans or basic liveness tests, are now vulnerable to sophisticated AI-driven fraud. For example, in April 2025, a security researcher demonstrated that an AI-generated passport created via ChatGPT successfully passed KYC checks on major fintech platforms like Binance and Revolut (Athmane Bouazzouni - Medium).
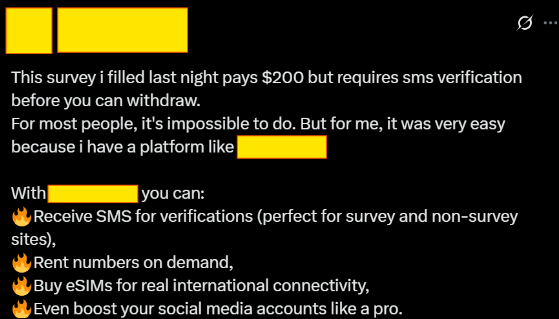
SMS Verification can be outsourced: The communities I observed regularly share services that provide temporary phone numbers for SMS verification.
Email Verification can be spoofed: With unlimited disposable email services and automated account creation tools, email verification only adds a few seconds to the fraud process.
The Tools That Actually Work
However, not all security measures are created equal, during my investigation, I noticed certain techniques that even sophisticated fraudsters struggle with:
Advanced Device Fingerprinting: While tools like GoLogin and MoreLogin can mask basic browser fingerprints, they struggle against advanced fingerprinting that analyzes hardware characteristics, canvas rendering, and behavioral patterns. The fraud communities frequently complain about "advanced tracking" that their tools can't defeat.
Cross-Platform Identity Correlation: The most effective approach I've seen combines multiple data points across different platforms and time periods. When a verification system can correlate identity signals across multiple touchpoints, it becomes much harder for fraudsters to maintain their fake personas.
The key insight is that fraudsters are always looking for the path of least resistance. They'll quickly abandon targets that implement comprehensive, multi-layered security in favor of easier marks still relying on outdated measures,
Looking Forward

I’d be remiss if I didn’t talk about the types of technology SuperMarketer is developing and how this can help. We use data from GDPR data exports, this is verified data directly from a respondent’s online accounts (e.g. Google, Amazon etc.).
While it can be easy to fake a telephone number or email address, it takes years to age an Amazon account to a point where it looks like it belongs to a legitimate human.
That kind of dataset contains rich, hard-to-fake signals that are ideal for spotting fraud:
Behavioral analysis grounded in real histories — instead of just measuring clicks or survey speed, researchers can check whether usage patterns resemble those of a genuine human account.
Advanced device fingerprinting — SuperMarketer’s data includes unique technical traces like device IDs, IP addresses and even the exact timestamp an account was created. These provide far stronger signals than anything a browser-spoofing tool can fake.
Cross-platform identity correlation — names, emails, and addresses that match across multiple online accounts add far more confidence than relying on a single declaration.
Real-time fraud scoring — by combining these factors, responses can be given a confidence rating before they’re accepted.
Final Thoughts
Online scamming communities demonstrate the sophisticated lengths fraudsters will go to exploit the market research industry.
As we continue developing detection and verification technologies at SuperMarketer, insights like these help us stay ahead of evolving fraud tactics. The battle between fraudsters and fraud detection is ongoing, but understanding the enemy's playbook is the first step in building better defenses.
This investigation was conducted purely for research purposes to better understand fraud patterns affecting the market research industry. No fraudulent activities were engaged in during this research.




Comments